Web application security is an ever-critical concern, and scanning for vulnerabilities should be seamlessly integrated into your CI/CD pipelines. If you’ve been searching for a way to automate OWASP ZAP (Zed Attack Proxy) scans and generate detailed, actionable reports in your Azure DevOps pipelines, you’re in the right place.
In this blog post, I’ll walk you through how to automate OWASP ZAP scans using Azure DevOps release pipelines. We’ll also explore how to transform the ZAP results into a format suitable for CI/CD integration. Let’s dive right in!
Defining Pipeline Environment Variables
The process begins by defining pipeline variables that will be used by the pipeline tasks. Here is a screenshot of the pipeline variables configuration:
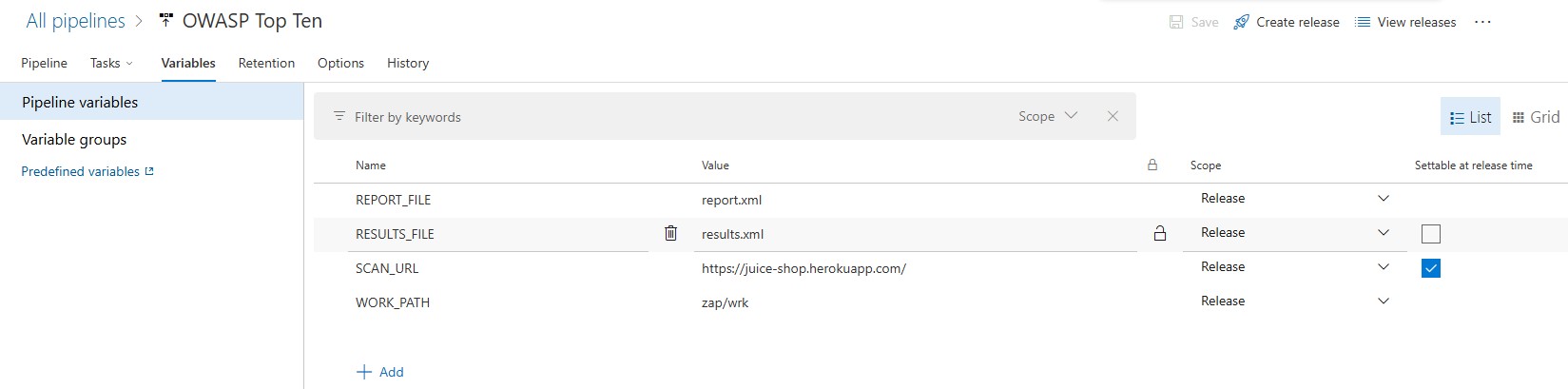
The following variables are defined:
SCAN_URL: This is the website URL that will be scanned by the ZAP scanner.REPORT_FILE: This is the file name of the report that will be generated by the ZAP scanner.RESULTS_FILE: This is the NUnit formatted file that will be generated by the transformation task.WORK_PATH: This is the folder in which theREPORT_FILEand theRESULTS_FILEwill be created.
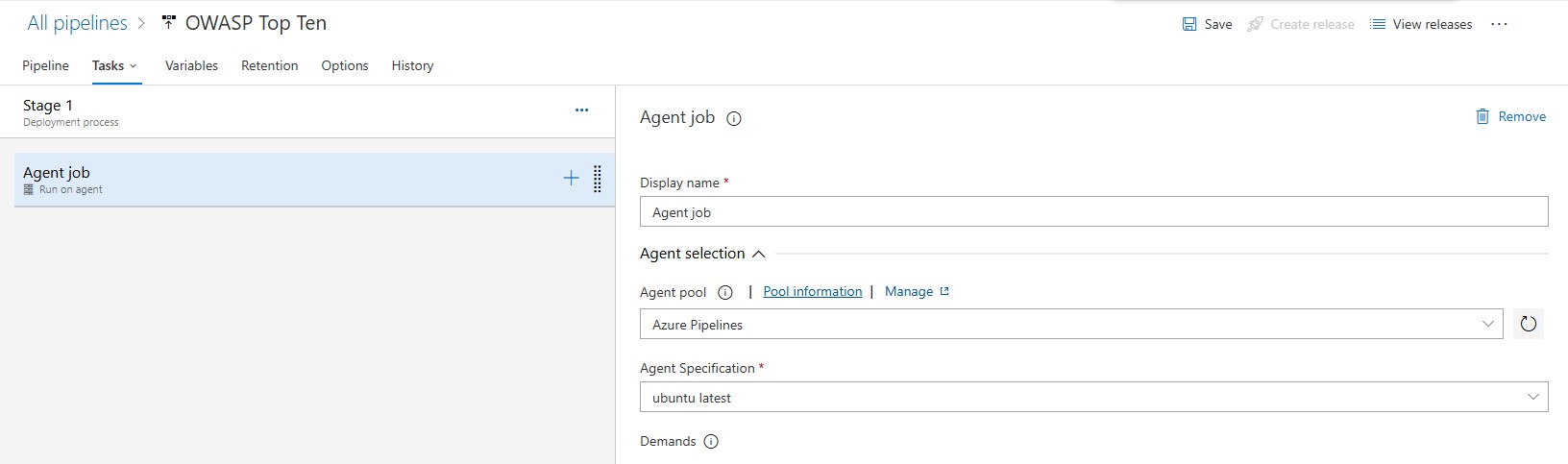
Defining the Agent Job
Next, it is important to define the correct parameters for the agent job. Since we are going to be running both Bash and PowerShell scripts, we will choose the Azure Pipelines agent pool and the ubuntu-latest agent specification as shown in the screen below:
Installing Docker in the Agent Machine
In order to run docker commands, the docker engine will need to be installed on the agent machine. This is done by adding the Docker CLI Installer task:
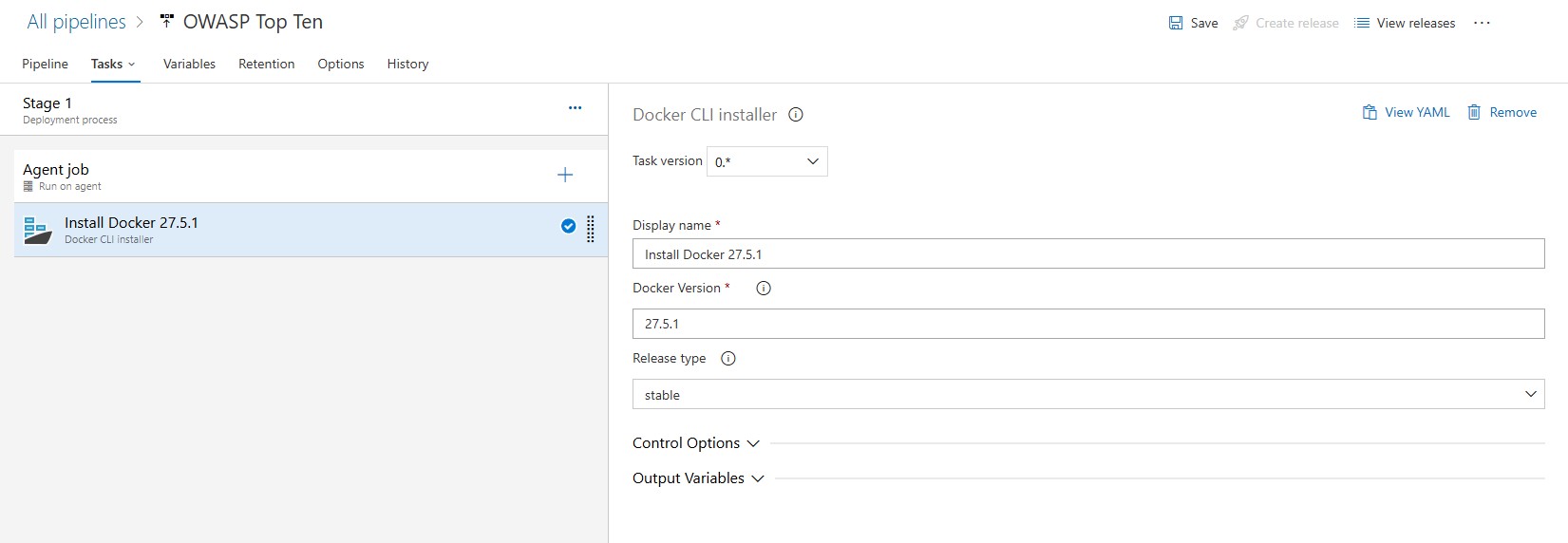
NOTE: Visit the Docker Engine release notes page to find the latest version of the docker engine.
Running the OWASP ZAP Docker container
The next step leverages a pre-configured OWASP ZAP Docker container:
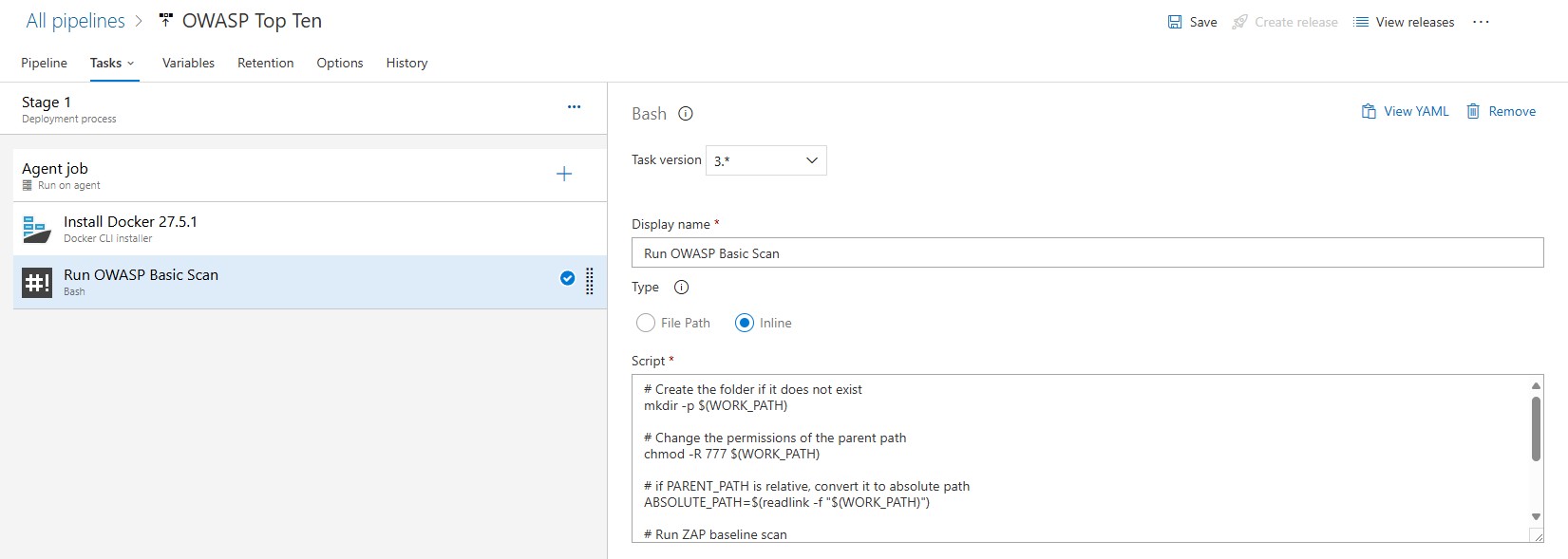
Using this container, we can run baseline scans against our web applications to detect potential vulnerabilities.
Here’s the full script for the baseline scan command:
| |
This command mounts a working directory to store the results and scans your application’s URL for common vulnerabilities. The results are generated in an XML format by default and stored in a file defined in the REPORT_FILE variable and located in the folder defined by the WORK_PATH variable.
Converting ZAP Results to NUnit Format
While the XML report is comprehensive, integrating its results into your pipeline can be tricky. To make this integration seamless, we’ll transform the ZAP results into NUnit format. NUnit is widely supported by CI/CD tools and allows for easy visualization of test outcomes.
In addition, we are only interested in the Top Ten OWASP Vulnerabilities, so this step also filters outcomes by the Top 10 categories.
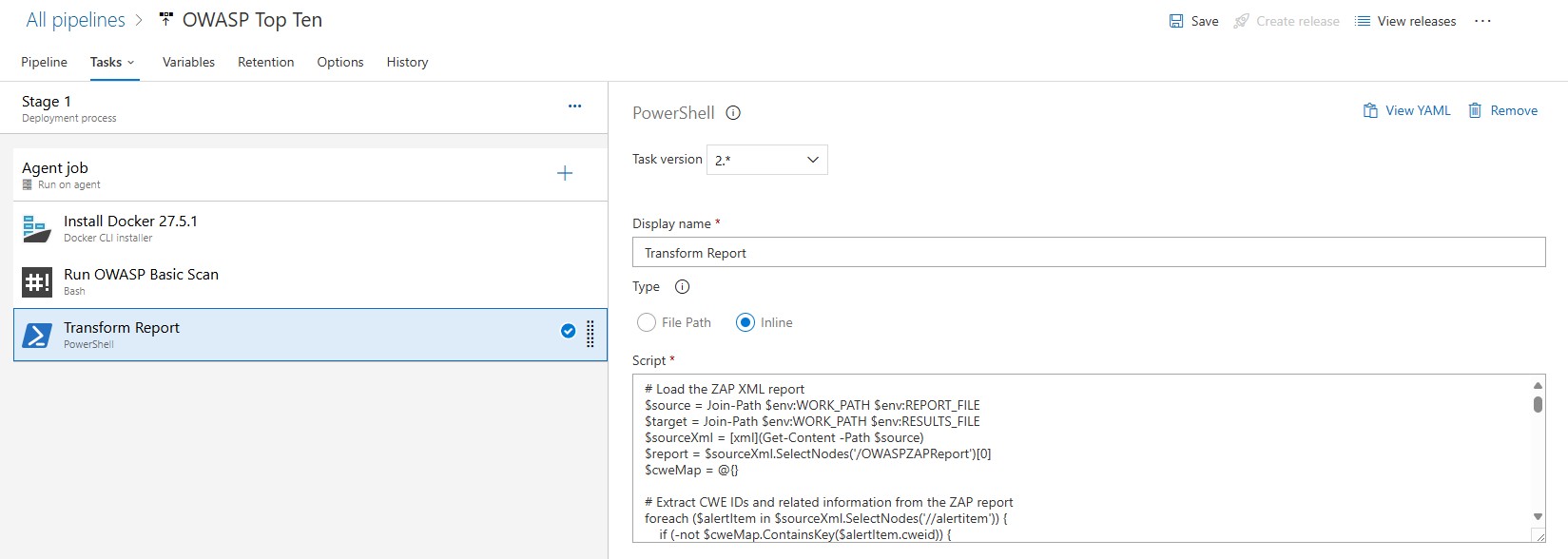
This is achieved using a custom PowerShell script. The script extracts key details from the ZAP XML report, maps vulnerabilities to the OWASP Top 10 categories, and converts the data into a structured NUnit report.
Here’s the script in action:
| |
Key Features of the Script
- Alert Aggregation: Gathers and organizes vulnerability data from ZAP results.
- OWASP Mapping: Links CWEs from ZAP alerts to OWASP Top 10 categories. For a comprehensive list of CWE IDs and their mappings to the OWASP Top 10 categories, you can refer to the official OWASP documentation: OWASP Top Ten Mapping.
- NUnit Format Conversion: Outputs the data in NUnit format for easy integration with Azure DevOps.
Integrating NUnit Results with Azure DevOps
Once the script generates the NUnit report (results.xml), it can be published in Azure DevOps as a test result. Add a task in your pipeline to publish the report:
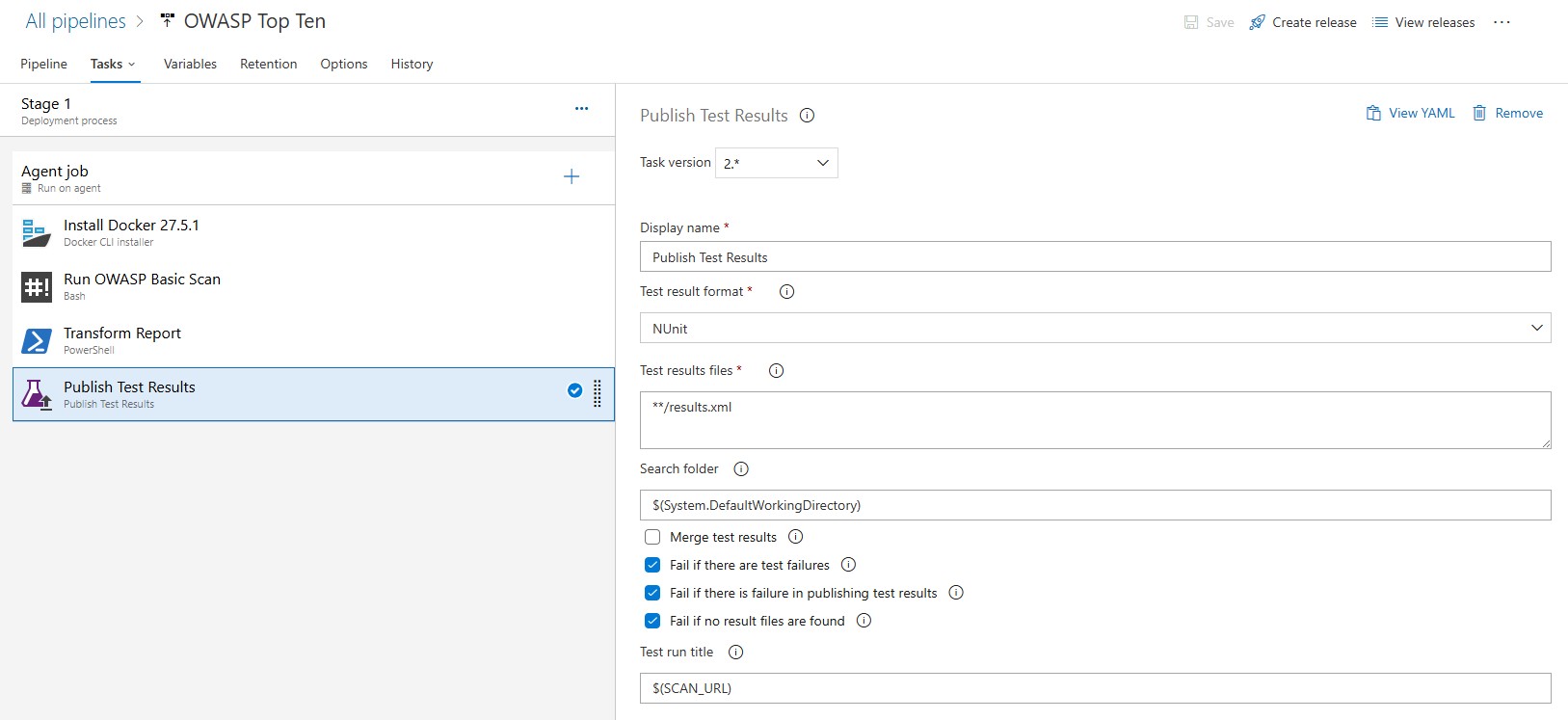
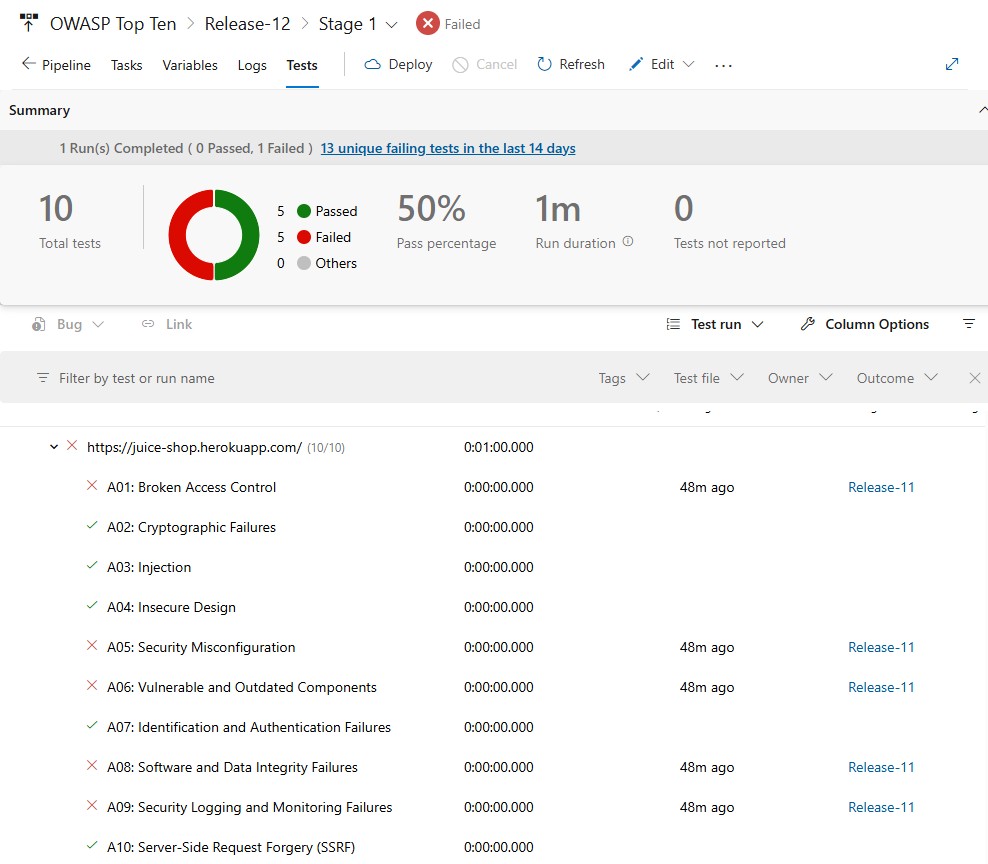
This step ensures that vulnerabilities are tracked as test failures, making them highly visible to your development and security teams.
Wrapping Up
By integrating OWASP ZAP scans with Azure DevOps, you’re not just automating security testing but embedding it into your development lifecycle. The PowerShell script transforms ZAP results into actionable insights that teams can immediately act upon, helping you stay ahead of security risks.
Are you ready to level up your CI/CD pipeline with automated security scans? Give this approach a try, and let me know how it works for you in the comments below.
Happy securing!
References:
